Implementation and Tools
The world of DevSec is divided into several areas according to the software development life cycle. There are tools and methods that lead the development and operation teams to keep our system secure.
During the project planning phase, we will allocate the necessary resources and time to implement in the development process practices that will prevent “bad” code from reaching creation. Code control with an emphasis on security issues, peer control and “clean-code” principles as much as possible.
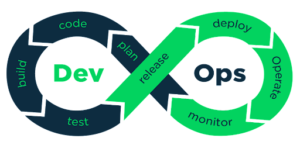
In the development phase, we integrate tools for code control, which scan the code we write in for search errors that may lead to security breaches. We use tools that know how to identify and rate the safety level of libraries and speed up the development process. In addition, we also avoid libraries that receive a low score, libraries that are rarely used and libraries that are not regularly maintained.
The use of automation processes of transferring the products between the environments while running automatic tests, implementing API Security tools already on the testing environment will enable the detection of suspicious inquiries even in the test environment.
The implementation of monitoring and security tools in the production environment with the help of integrated teams of development, security and DevOps personnel enables a short circuit closure to provide solutions to the projects changing needs.
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.
Strategic Partners



Technology Partners


















Our Clients




























