The DevSecOps Pain Pyramid
The benefits of integrating information security into DevOps processes are numerous – protection against new attack vectors, reduction of friction with engineering and development teams. All of this ensures that teams solve the most dangerous problems first, and meet regulatory requirements.
However, it’s not as easy as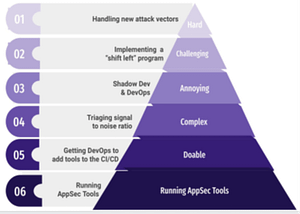 snapping your fingers and watching DevSecOps take control of the process. There are several challenges that any successful DevSecOps program must address when trying to secure today’s software supply chain. The “pyramid of pain” includes trivial challenges, such as running appsec tools, and very difficult challenges, such as protecting against new attack vectors.
snapping your fingers and watching DevSecOps take control of the process. There are several challenges that any successful DevSecOps program must address when trying to secure today’s software supply chain. The “pyramid of pain” includes trivial challenges, such as running appsec tools, and very difficult challenges, such as protecting against new attack vectors.
How does the OX.Security solution help deal with the pain pyramid?
OX helps DevSecOps manage the pain pyramid. OX is the first company in the field of supply chain security that helps DevSecOps manage end-to-end information security. The platform is the first to move beyond SBOM and use the PBOM security standard to provide security coverage for every stage of the development pipeline, from the earliest planning stages to deployment to deployment. OX integrates seamlessly with existing tools and infrastructure and gives DevSecOps teams full visibility and control over the attack surface,
Includes: source-code, pipeline, artifacts, container images, runtime assets, and applications.
What are the components of the solution:
Discovery: OX provides a complete inventory and automatic discovery process of the corporate applications, the build processes and the production infrastructure.
Prioritization: Do the professional teams fix the important ones? Focus on taking advantage of the most dangerous things first. OX automatically blocks vulnerabilities found in the pipeline such as blocking code connection in the process.
Security: Do you trust the artifacts in production? Enforce security policies from cloud to code, identify any unidentified components and ensure all processes come from a trusted source.
Automation: How much work is done manually? Continuous monitoring of changes in your environment that affect the security of th
The benefits of integrating information security into DevOps processes are numerous – protection against new attack vectors, reduction of friction with engineering and development teams. All of this ensures that teams solve the most dangerous problems first, and meet regulatory requirements.
However, it’s not as easy as snapping your fingers and watching DevSecOps take control of the process. There are several challenges that any successful DevSecOps program must address when trying to secure today’s software supply chain. The “pyramid of pain” includes trivial challenges, such as running appsec tools, and very difficult challenges, such as protecting against new attack vectors.
How does the OX.Security solution help deal with the pain pyramid?
OX helps DevSecOps manage the pain pyramid. OX is the first company in the field of supply chain security that helps DevSecOps manage end-to-end information security. The platform is the first to move beyond SBOM and use the PBOM security standard to provide security coverage for every stage of the development pipeline, from the earliest planning stages to deployment to deployment. OX integrates seamlessly with existing tools and infrastructure and gives DevSecOps teams full visibility and control over the attack surface,
Includes: source-code, pipeline, artifacts, container images, runtime assets, and applications.
What are the components of the solution:
Discovery: OX provides a complete inventory and automatic discovery process of the corporate applications, the build processes and the production infrastructure.
Prioritization: Do the professional teams fix the important ones? Focus on taking advantage of the most dangerous things first. OX automatically blocks vulnerabilities found in the pipeline such as blocking code connection in the process.
Security: Do you trust the artifacts in production? Enforce security policies from cloud to code, identify any unidentified components and ensure all processes come from a trusted source.
Automation: How much work is done manually? Continuous monitoring of changes in your environment that affect the security of the organization. Prevention of dangerous code and configuration changes (configurations) to ensure that the corporate environment does not move from a secure state to an insecure state.e organization. Prevention of dangerous code and configuration changes (configurations) to ensure that the corporate environment does not move from a secure state to an insecure state.
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.

