What is F5?
F5 acquired Shape Security. But what is Shape Security and how does it contribute to the cloud information security of the organizations.
Shape Security protects against malicious automations that try to harm websites and mobile applications.
Attackers use automations for all kinds of purposes for malicious attacks. One of the most common and expensive attacks is credential stuffing. On average, over eight million usernames and passwords are reported stolen per day. Attackers attempt to use these privileges on many sites, including those of financial institutions, retail, airlines, hospitality, and other industries. Since many people reuse usernames and passwords on many sites, these attacks are incredibly successful. And considering the scope of the activity, the criminals rely on automation to carry out the attacks.
Besides credential stuffing, attackers use automations to create fake accounts, scrapping information, verifying stolen credit cards and all kinds of fraud. The losses include system downtime due to a heavy load of bots, financial liability from account takeover and loss of customer trust.
How does it work?
Shape is always learning and adapting itself. Rather than relying on a single static 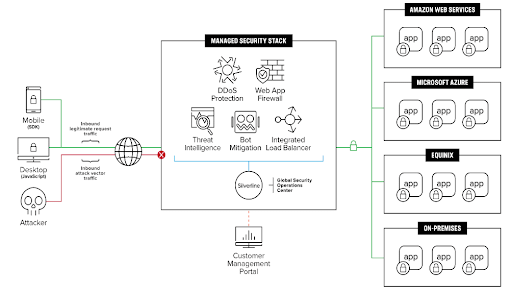
countermeasure, Shape’s system is strategically designed for continuous learning and adaptation.
The Shape solution is integrated into mobile and web applications with signal collection code covering both the browser environments and user behavior. A real-time rules engine processes these signals to detect bot activity and manage the attacks. These signals are fed into a data system that runs many machine learning systems, whose findings, guided by data scientists and domain experts, expand the development of new signals and new rules, always improving the quality of data and decisions.
Shape has been protecting a large part of the Fortune 500 clients for several years, while at war with the most advanced and persistent attackers, it has gone through many learning cycles, developed a very rich signal and rule system and perfected the learning process. Stopping the bots depends on the impact of learning gained from protecting many organizations and analyzing huge amounts of data.
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.











