What is Microsoft 365 E5?

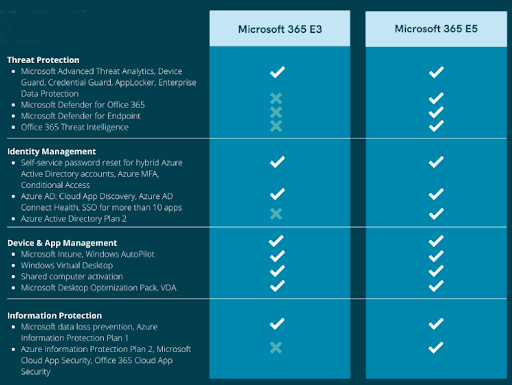
Microsoft 365 provides a suite of productivity apps. Microsoft 365 E5 is an enterprise-level version of this suite. In addition to productivity apps, E5 offers Microsoft security technologies and advanced compliance and analytics capabilities. Here are key features of Microsoft 365 E5:
Security—Microsoft 365 E5 provides integrated and automated security capabilities to protect identity and threats. This can help prevent attacks from doing significant damage.
Compliance—Microsoft 365 E5 consolidates data protection and compliance capabilities to help control and protect data. This can help minimize risk and meet regulatory and corporate compliance requirements.
Analytics—Microsoft 365 E5 offers Power BI capabilities that can help analyze your data and generate insights. You can use Power BI to realize new business value.
What are Microsoft 365 E1 and E3?
כThis is the “Basic” version of the Office 365 enterprise plan. It includes the following features:
Microsoft Exchange email and calendar management.
– Yammer for corporate social messaging.
– SharePoint for intranet capabilities and team sites.
– OneDrive for Business includes 1 TB of storage.
– Microsoft Delve for content search.
– StaffHub for task management.
– Microsoft Stream for corporate video sharing.
– Microsoft Teams for chat and video conferencing.
– Online versions of all Microsoft Office applications – Word, Excel, PowerPoint, etc.
Microsoft Office E3
The E3 plan has the same features as E1 and the following additional features:
Use of multiple devices – each user can install applications on up to 5 desktop computers, 5 tablets and 5 smartphones.
Microsoft Office Suite – Users are entitled to the latest versions of all Microsoft Office applications, which they can download and install on Windows, Mac, tablets, and smartphones.
Cloud storage—Ability to increase OneDrive storage to 5 TB or 25 TB.
Data Leak Prevention (DLP) – supports compliance with regulations and standards, by protecting sensitive data and preventing its transfer outside the organization.
Advanced data management – including archiving, rights management, document encryption and advanced access controls for documents and e-mail.
Microsoft Defender for Endpoint P1 – The E3 license includes the basic version of Microsoft Defender for Endpoint (known as Plan 1), which provides next-generation anti-malware, attack surface reduction (ASR), and granular control over endpoint access and behavior.
Microsoft 365 E5: Top 10 Security Features
The E5 plan provides all the features included in the E3 plan along with extended security features. Here is a brief overview of security features unique to Microsoft 365 E5:
- Azure Active Directory Premium 1 & 2
Azure Active Directory (Azure AD) is a cloud-based identity and access management (IAM) feature built into the Microsoft 365 ecosystem. It provides single sign-on (SSO), which allows employees to use a single set of credentials to access Microsoft 365 resources. In addition to multi-authentication capabilities Factors to protect user accounts.
Azure AD offers a Premium P2 plan that includes an identity protection feature. Identity Protection can detect potential identity breaches and automatically respond to suspicious actions. which allows you to configure these automatic responses to ensure that the responses conform to your security standards. You can also manually investigate and mitigate suspicious events.
Microsoft Defender for Office 365 Microsoft Defender for Office 365 offers the following security capabilities: Email Filtering – This solution provides cloud-based email filtering that protects against threats to email and collaboration tools, such as phishing schemes, malware attacks, and business email compromise. Investigation – Defender for Office 365 offers threat hunting, investigation, and remediation capabilities. It can help detect, investigate, prioritize, and respond to threats.- Information Protection and Governance Microsoft uses the following two services to classify and protect data across all locations:
Microsoft Information Protection (MIP)—This solution helps discover, classify, and protect sensitive data and business-critical content throughout its lifecycle and across all locations in the organization.
Microsoft Information Governance (MIG)—This solution manages the lifecycle of content through various solutions for classifying, importing, and storing business-critical data. Which helps control data and maintain compliance with regulatory and organizational requirements.
- Insider Risk Management
Microsoft 365 E5 offers insider risk management to help you minimize insider risks. It provides detection, investigation and response to malicious activities and errors. The solution allows you to use policies to define specific risks that are relevant to your organization. For example, you can set up automation to run in certain cases, as well as upload cases to Microsoft Advanced eDiscovery when necessary.
- Power BI Pro
Power BI consists of a variety of services, connectors, and apps that work together to transform multiple data sources into interactive and visually immersive insights. You can easily connect data sources to Power BI and visualize to discover and share insights. This will allow you to use various data sources, including Excel spreadsheets, cloud-based, on-prem and hybrid data warehouses.
- Microsoft Defender for Endpoint
Microsoft 365 E5 lets you use the capabilities of Microsoft Defender for Endpoint to detect, prevent, investigate, and respond to advanced threats.
- Microsoft Defender for Identity
Microsoft 365 E5 employs Microsoft Defender for Identity to provide cloud-based identity security capabilities. This solution uses local AD signals to detect and investigate compromised identities, malicious insider operations, and advanced threats.
- Microsoft Defender for Cloud Apps
Microsoft 365 E5 uses Microsoft Defender for Cloud Apps to provide Cloud Access Broker (CASB) capabilities. It supports multiple deployment modes, such as log collection, reverse proxy, and API connectors. Once connected, this CASB provides extended visibility and control over data travel. It also offers sophisticated analytics to detect threats across all cloud services, including Microsoft and third-party clouds.
- Advanced eDiscovery and Advanced Audit
Advanced eDiscovery helps collect, preserve, review, analyze and export content required for internal and external investigations. Microsoft 365 builds on existing analytics capabilities and Microsoft eDiscovery to help legal teams manage the legal lien notification workflow and communicate with the people involved in the case.
Microsoft 365 provides an Audit capability that offers visibility into various audited activities in Microsoft 365 services. This helps manage Compliance and legal investigations by facilitating the following:
Increased audit log retention, more time is retained for investigative purposes.
Access important events to help determine the scope of the breach.
Faster access to the Office 365 Management Activity API.
- Built-in Third-Party Connectors
Microsoft 365 offers built-in third-party data connectors (connectors) to let you import and archive from various sources, such as social media platforms like Twitter. These connectors support an internal risk management solution that allows you to archive data in the Microsoft 365 Compliance Center.
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.