Zero Trust Deployment
Zero Trust is a new security model that assumes there may be vulnerabilities in the organization and verifies every request as if it originated from an uncontrolled network; regardless of the origin of the request or what resource it accesses.
The Zero Trust model teaches us to “never trust, and always verify”.
Zero Trust Security Architecture
The Zero Trust approach is spread over all the digital resources of the digital organization and serves as a complete security philosophy and an end-to-end prevention strategy.
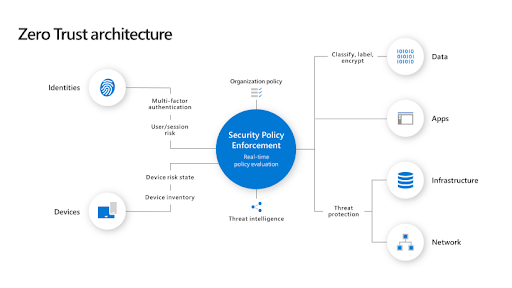
Security policy enforcement is at the core of Zero Trust architecture. This includes Multifactor Authentication with Conditional Access that considers user account risk, device status, and other criteria and policies the organization defines.
Identities, devices, data, applications, network, and other infrastructure components are all configured with appropriate security. Policies defined for each of these components are aligned with the overall corporate Zero Trust strategy. For example, a device policy sets the criteria for “healthy” devices and conditional access requires these devices to access specified applications and data only.
Threat protection and security intelligence monitor the environment, flood current risks, and take automated action to prevent attacks.
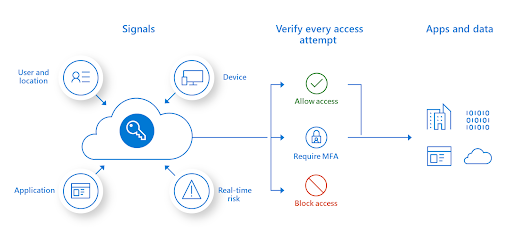
The Zero Trust Approach
Zero Trust is a new security model that assumes there may be vulnerabilities in the organization and verifies every request as if it originated from an uncontrolled network; regardless of the origin of the request or what resource it accesses.
The Zero Trust model teaches us to “never trust, and always verify”.
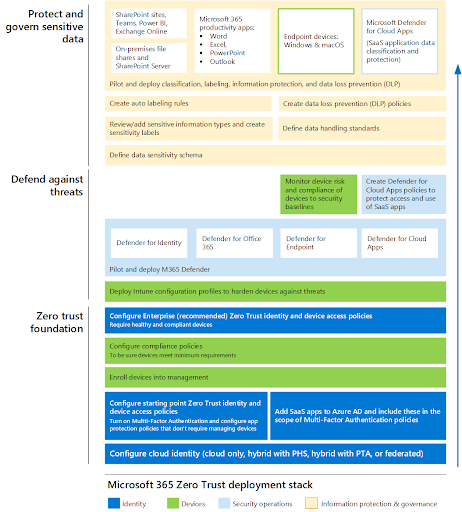
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.
Strategic Partners



Technology Partners


















Our Clients




























