APIs-the dominant target in today's application environments.
APIs are at the heart of today’s modern applications, their job being to help organizations connect with customers and partners, increase revenue, and assist with digital transformation initiatives. APIs have also become the leading application destination for attackers, as countless high-profile attacks show. Gartner predicts that ” by 2022, API misuse will move from a rare attack vector to a very frequent attack vector, resulting in data breaches for enterprise Web applications.”Traditional solutions including WAFs and API Gateways cannot protect your API from today’s attacks.
אז מה עושה SALT Security?
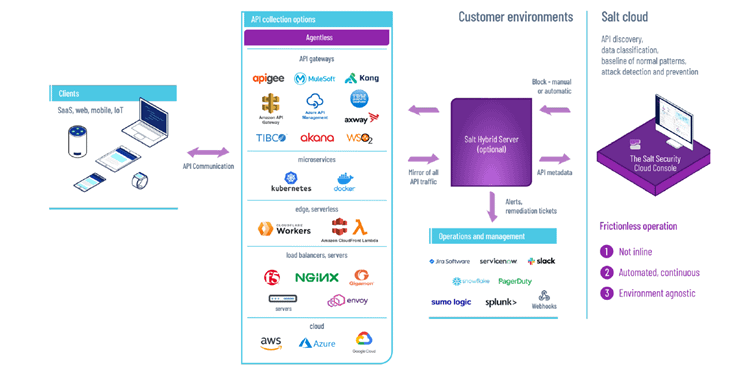
SALT Security The SaaS solution provides an end – to-end solution in the API Security worlds. The solution provides a systemic view of all open APIs in an organization, mapping a client’s attack area, identifying attackers at a very early stage of their research, and the ability to block attacks and provide ways to help improve security in the API.
SALT uses BIG DATA engines and Machine Learning techniques to correlate all unusual requests, track an attacker over time, and give the organization the opportunity to understand who the attacker is, what unusual things he is doing, and how he can be stopped before anything significant happens.
SALT has been ranked by Gartner and its customers as “the world’s leading API security with real-time behavior analysis” for its ease of interfacing, deploying, managing and maintaining the solution.
How does the process work?
Step one – Collect all the data on the client’s API. We collect a copy of the traffic from all kinds of sources (load balancers, gateway api, Kubernetes) . & nbsp;The collection is not carried out inline so it does not interfere with the day-to-day work.
STEP TWO-YOU FEED all the INFORMATION into our BIG DATA ENGINE. This engine does analysis on all traffic all the time.
Phase C Above this, the system activates the AI and ML to produce a baseline that is suitable for the client’s environment, the client’s specific API, the client’s specific users, etc.
What is the solution for the customer?
- DISCOVERY – WE MAKE DISCOVERY OF ALL THE APIs, and MAP THE ATTACK SERFACE OF THE SAME CLIENT. Visionity of all the API.
- RUN TIME PROTECTION-We IDENTIFY attackers at A VERY EARLY STAGE OF THEIR RESEARCH, AND ALLOW CUSTOMERS TO BLOCK ATTACKS.
- SHIFT LEFT-Stopping the process and returning it to an earlier stage to correct the deficiencies.
So how can YouCC technologies help you?
- Architecture planning and implementation of solutions a. Cloud information from a variety of security system manufacturers.
- Microsoft Azure Security and Microsoft 365 capabilities.
- DevSecOps, design and implement security architecture in the cloud and container-based NGINX+world.
- Implementing business solutions that enable technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Offering a managed model for the delivery of information technology services and solutions to be carried out in an ongoing and efficient manner.
Interested in your organization's cloud security?
Looking for services in the cloud field? A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so we can get to know you, understand your needs and provide you with the best service.
Strategic Partners



Technology Partners


















Our Clients