Cider Security
Cider provides an end-to-end information security solution for all organizational CI/CD processes. The solution provides:
End-to-end visibility: Gain detailed visibility into engineering technologies, systems, and processes, all the way from code to production.
Seamless integration: Easily connect Sider to your process systems and seamlessly integrate security without disrupting corporate development and engineering processes.
Contextual Security: Optimize the security of your CI/CD processes, based on a preferred set of risks and recommendations tailored to your environment.
So how does CIDER do it?
- Build a complete “technical DNA” of your engineering environment
Cider seamlessly integrates with all systems across your CI/CD and provides you with a comprehensive and accurate analysis of all technologies, frameworks and integrations present in the environment.
- Map your ways to production:
Cider maps all the smart connections within your environment to create end-to-end visibility throughout the complete CI/CD journey – all the way from the SCM user to the artifact deployed to production.
- Reduce your CI/CD attack surface
Evaluate the layout of your systems and engineering processes. Analyze your environment against realistic attack scenarios and identify the controls required to reduce your CI/CD attack surface.
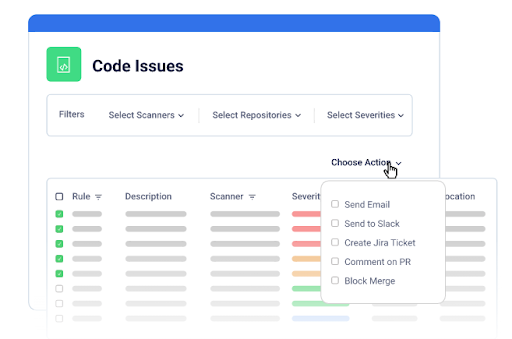
- A marketplace tailored to your DNA
Cider’s marketplace allows you to easily integrate multiple scanners and engines tailored to the specific needs and characteristics of your environments – allowing you to maintain strong and comprehensive oversight and security over the code and assets you move to production.
- Clear the noise and fix
Cider groups all code issues from our market scanners under a single pane of glass, enabling easy and efficient prioritization of patching activities across your development contexts. Issues are automatically identified and escalated to the appropriate owner using our automated workflows.
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.
Strategic Partners



Technology Partners


















Our Clients




























