What is F5 Advanced WAF?
Cyber-attacks are the leading cause of breaches and data theft. Despite the best efforts of secure application management and patching processes, half of all applications tend to remain vulnerable.
WAF systems are designed to protect the corporate applications from information breaches by fixing weak points and stopping attacks. F5® Advanced Web Application Firewall™, provides protection against application attacks through protection against malicious bots, encryption at the Application-layer level, SAPI Inspection, and behavior analysis.
Behavioral analysis is a basic requirement for detecting combined attacks. (Many layer 7 distributed denial-of-service) (DDoS) attacks are hidden (“stale”) and cannot be detected by signatures.
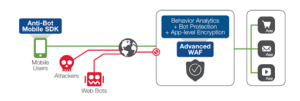
Advanced WAF automatically learns application behavior, then combines traffic behavioral heuristics with server loads to determine if conditions exist for a DDoS attack. This process provides the most accurate identification without false positives. Dynamic signatures are generated accordingly and deployed on the fly for real-time protection.
F5 Advanced WAF Features Proactive Bot Protection?
Proactive bot protection: Proactive protection against automatic bot attacks and various attack tools. This prevents layer 7 DoS attacks, web scraping, and brute-force attacks.
Data Protection: Protect sensitive information from being intercepted by encrypting data while it is still in the browser. Data Safe encrypts data at the application layer to protect against malware and keyloggers.
Behavioral DoS: Provides automated protection against DDoS attacks by analyzing behavioral traffic using machine learning and data analytics. By continuously monitoring the health of the server as well as load, anomalies (performance slowdowns or traffic increases) can be accurately identified and prevented by decision.
Flexible deployment: Available as a dedicated appliance, cloud-ready virtual appliance, or part of the F5 Silverline service.
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.
Strategic Partners



Technology Partners


















Our Clients




























