What is F5 Service Mesh?
The F5® Distributed Cloud Mesh Service Mesh is a centrally managed global proxy and load balancer with service discovery, service health checking, application micro-segmentation and application policies providing the most advanced implementation of an edge load balancer with ingress/ egress to any network service.
Service discovery integrates with multiple service managers like Kubernetes, Consul, or DNS along with health check support for http/https, tcp, custom, etc.
Endpoint health is distributed to all sites where the virtual service is exposed using extensions to the BGP protocol and this provides us with valuable insight into how to globally distribute load balancing activity.
Support for both TLS and Mutual TLS for authentication with policy-based authorization (policy-based authorization) in the proxy provides the ability to enforce end-to-end security of all handled application traffic.
In addition, the proxy gives, during an event, the ability to terminate user traffic in the F5 Distributed Cloud global network and use a persistent connection. Serve endpoints to enable the most optimal load balancing for the endpoints. It is a service available ready and accessible when an F5 Distributed Cloud Node or Cluster is deployed in an enterprise.
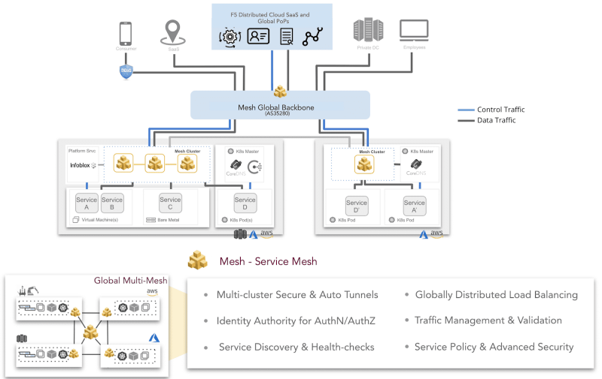
Main features in the Service:
- Multi-cluster Secure & Auto Tunnels
- Identity Authority for AuthN/AuthZ
- Service Discovery & Health-checks
- Globally Distributed Load Balancing
- Traffic Management & Testing
- Service Policy & Advanced Security
So how can YouCC Technologies assist you and your organization?
- Architecture planning and implementation of information security solutions from a variety of security system manufacturers to the cloud.
- Implementation of Microsoft Azure Security and Microsoft 365 capabilities.
- Building a DevSecOps array, planning and implementing a security architecture in the world of the cloud and containers based on NGINX+.
- Implementing business solutions that allow technology to be an ENABLER for your organization.
- Developing end-to-end solutions in the cloud environment and bringing modern capabilities to the development environment.
- Proposing a managed model for the provision of services and solutions in the field of information technologies to be carried out in a regular and efficient manner.
Interested in your cloud security?
Looking for A company that will accompany you personally, professionally and without compromise? Let's talk!
Leave us your details so that we can get to know you, understand your needs and match you with the best service.
Strategic Partners



Technology Partners


















Our Clients




























